After Shapella: Is Distributed Validator Technology (DVT) the Next Narrative for ETH?
Breaking down DVTs - the important trend you should be paying attention to
Introduction
Since Ethereum’s Merge, we have witnessed the Liquid Staking Derivative (LSD) narrative flourish. More recently, a significant milestone in Ethereum's development came with the Shanghai-Capella upgrade, which enabled the withdrawal of staked ETH, marking a critical juncture in its roadmap.
The rapid expansion of the liquid staking market, however, has led to concerns about concentration. For instance, Lido and Coinbase collectively control 90% of the ETH liquid staking market (Lido alone claims 75% of the market).
Liquid staking protocols have the power to allocate ETH to validators and manage the staking and withdrawal processes, which could have direct impacts on Ethereum's network security. This concentration of power raises concerns about the long-term implications for the Ethereum ecosystem. As the liquid staking market evolves, addressing these risks is crucial for maintaining the network's security and ensuring a healthy, decentralized future.
Following the success of The Merge and the ascent of liquid staking, the market is now eagerly seeking the next big narrative to unfold after the Shanghai upgrade.
One concept highlighted in Vitalik’s Ethereum roadmap is Distributed Validator Technology (DVT), which is a system that distributes the job of an Ethereum validator among a set of distributed nodes.
As the community anticipates the next breakthrough, could DVT emerge as an extension to the liquid staking narrative?
In this memo we seek to explore:
How do validators secure the Ethereum network?
What are the issues with current staking methods?
What is Distributed Validator Technology (DVT)?
Why do we need DVT and what is its purpose?
2 projects in the DVT space
Is DVT the next big narrative for Ethereum?
Blockchain scaling beyond execution layer
First let’s recall the idea of a modular blockchain, which states that a blockchain have different functions that can be dis-aggregated into separate layers, namely the execution layer, consensus layer and data availability layer:
Execution Layer- This layer handles transaction processing and state computation, with nodes executing pending transactions and updating the blockchain's state.
Data Availability Layer - This layer focuses on the data stored in each block of the blockchain, ensuring that all information is published and publicly accessible across validating nodes.
Consensus Layer - This layer ensures that all validating nodes agree on the same "state," maintaining the order, rules, and state of the blockchain as agreed upon by a majority of participants.
Scalability remains a central issue in the blockchain ecosystem, and while much of the conversation focuses on the execution layer, it is crucial to recognize that scaling extends beyond this layer.
Solutions like roll-ups and Layer 2 primarily address scaling challenges within the execution layer, but advancements in other layers, such as Data Availability (DA), also play a significant role. For instance, 'data availability sampling' is a mechanism that ensures the data for a proposed block is available without requiring the entire block to be downloaded.
Equally important, though often overlooked, is the scaling of the consensus layer. The security and stability of a blockchain rely on the number and diversity of validators hosting it. Distributed Validator Technology (DVT) can thus be seen as a way to scale the consensus layer, enhancing accessibility and fostering greater participation among validators.
How do validators secure the network?
Before we dive into DVT, let’s recap on how staking works on Ethereum.
Ethereum staking is a process in which users of the network engage in the Proof-of-Stake (PoS) consensus. To partake in staking, users must deposit a minimum of 32 ETH to activate validator software. By staking their ETH, users contribute to securing the network and, in return, earn rewards. Validators play the role of storing data, processing transactions, and validating blocks on the blockchain. To better understand the distinctions between validators, nodes, and clients within the context of blockchain, consider the following definitions:
Node: A node refers to any instance of client software connected to other computers running the same software, thus forming a network. To run a node, one must first download an Ethereum client application.
Client: A client is an implementation of the blockchain that verifies data against the protocol rules and maintains the network's security. A client refers to the software needed for Ethereum nodes to read blocks on the blockchain and interact with Ethereum-based smart contracts.
Validator: A validator is a specific type of node that participates in the blockchain's consensus mechanism by confirming the legitimacy of transactions.
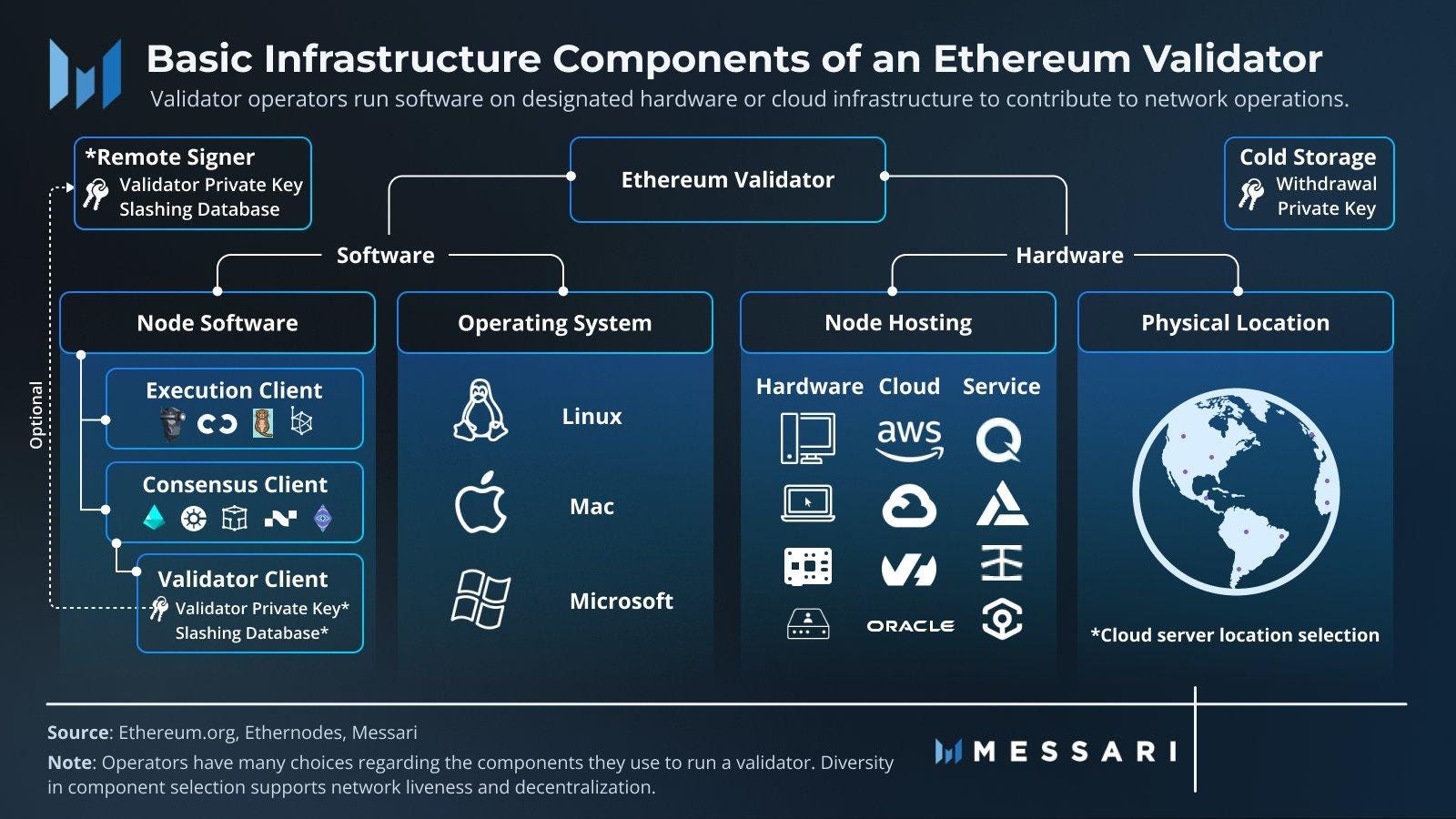
Becoming an Ethereum validator involves a multitude of choices and considerations, both on the hardware and software fronts. On the hardware side, factors such as the physical location of the node and the decision to self-host or utilize a cloud service must be taken into account.
Regarding software, validators must consider the node software being used and the operating system on which it runs. Each component in this process could represent a potential point of failure. For example, by opting to host nodes on a cloud service like AWS, validators introduce counte rparty risk from Amazon. The illustration below provide a summary of the infrastructure components of an Ethereum validator.
What are the issues with current staking methods?
Now we have explained how validators work, what are the actual ways to stake ETH? Currently there are four main staking methods:
Solo Staking: Self-hosted validator node with full control, but requires 32 ETH and hardware. Bear risk of penalties for being offline and malicious behavior.
Staking as a Service: Third-party operator handles hardware and node operations, still requiring 32 ETH, but users hand off validator keys. Introduces third-party risk. Fees are deducted from rewards.
Pooled Staking: Users deposit ETH into a pool, and a third-party operator handles all validator duties. Low entry but operator takes a percentage of yields.
Centralized Exchanges: Straightforward setup, no minimum amount required, usually have the lowest rewards. Staked assets managed by exchanges, less transparency, higher risk from platform hacks, poor management, etc.
Here is a comparison of the staking methods:
As we can see, each staking solution has trade-offs in different aspects. While running a solo validator is best for network diversity, it requires users to securely store their private keys. Losing access to these private keys can lead to a single-point-of-failure.
Furthermore, validator liveness checks play a crucial role in ensuring the stability of the Ethereum network. When a validator client fails to sign messages for any reason—be it network disruptions, cloud failures, software crashes, or hardware issues—they face penalties in the form of lost staked balances. This can occur due to inactivity or double-signing instances.
To mitigate these risks, staking services offer an alternative for users, allowing them to avoid the hassle of setting up and maintaining a solo validator. However, this convenience comes at a cost. When opting for staking services, users must hand over their private keys to the service provider and place full trust in the operator.
Another issue with more centralized staking methods is regarding client diversity. As mentioned in the previous section, validator nodes have to run two client software. The execution client is responsible for monitoring new transactions broadcasted within the network and executing them in the EVM. On the other hand, the consensus client allows the network to reach consensus based on the validated data provided by the execution client.
As we can see, Prysm and Lighthouse are the dominant consensus client used by 77% of validators. For the execution clients, the concentration is even worse with Geth alone making up 60%. Such concentration in specific clients could prove dangerous for the network.

Why is this dangerous? This is because to achieve finality, two-thirds of validators must agree. If a client controlling over 66% of the market share experiences a bug and forks onto its own chain, it can finalize the fork instead of the real chain.
In April 2021, a bug in the Prysm client led to approximately 14% of validators going offline and around 70% of blocks being missed for nearly two hours. Most validators using Prysm were unable to produce new blocks during this period, affecting their profitability. Although no validators were slashed, the incident underscored the risks associated with infrastructure concentration.
In the following sections let’s explore what DVT is and how it could address the pinpoints in current staking methods and the issue of infrastructure concentration.
What is DVT?
The basic idea is that DVT enhances the resiliency and security of Ethereum validators by enabling them to run on multiple nodes, thus reducing risks like slashing. DVT allows a cluster of nodes to act collectively as a single validator. The result is a more robust and accessible staking experience for all validators.
Let’s look at a more technical definition and unpack it step by step.
DVT distributes the job of an Ethereum validator among a set of distributed nodes using a blend of 1) distributed key generation, 2) Shamir's secret sharing, 3) multi-party computation and 4) Byzantine fault-tolerant algorithms to improve resilience and maintain the integrity of the network.

Distributed key generation
Distributed key generation (DKG) is a process that involves multiple parties working together to calculate and generate a private key, ensuring that no single member has full control over the key. The private key is encrypted and divided among all participants, enhancing security and preventing unauthorized access.
Typically, the nodes involved in a DKG are non-trusting, which means that their operators do not need to know or trust one another. This creates a sufficient level of fault tolerance and paves the way for the implementation of threshold signing schemes.
Shamir's secret sharing and threshold signing
Shamir's secret sharing is an algorithm for distributing private information or a secret among a group in such a way that the secret can be reconstructed only when a sufficient number of shares are combined together. It enables the private key to be divided among participating validator clients, with no single share being sufficient to sign messages. This prevents any single point of failure and ensures that the network can continue to function even if some nodes are compromised.
For instance, in a DVT setup with four operators and a threshold of 3 out of 4, if one computer goes offline or is untrustworthy, the remaining three nodes can still sign messages and maintain the network's functionality.
If you have watched Harry Potter, you can think of it as a horcrux. Horcruxes are magical objects that contain fragments of Voldemort’s soul, protecting him from being destroyed. To defeat Voldemort, all of the Horcruxes must be found and destroyed. Similarly, secret shared keys involve breaking up the original key into multiple pieces, each held by a different node or participant. Just as with Horcruxes, an attacker would need to gain control over multiple pieces to effectively control or steal the key.
Multi Party Computation (MPC)
MPC enables contributing operators to utilize their secret shares for signing messages and performing calculations without ever reconstructing the complete secret on any individual device. As a result, the risk of centralizing the private key during computation is eradicated, preserving the decentralized nature of the distributed validator setup.
BFT Consensus
This component refers to the process of the machines performing validator duties in a distributed validator “cluster.”
Imagine a group of friends at a party trying to agree on what pizza to order. Beacon nodes in a DVT setup are like these friends, working together to maintain the harmony of the network by assigning duties to validator clients. They use a method called threshold cryptography to divide the responsibility of holding a private key, ensuring that no single friend—or Beacon node—controls the entire decision-making process.
The Istanbul Byzantine Fault Tolerance algorithm is like the designated decision-maker in this group of friends, responsible for suggesting a pizza choice (proposing a block) and sharing it with the rest of the group. If at least 66% of the friends (Beacon nodes) agree on the pizza choice, it becomes the final decision (added to the blockchain).
If the designated decision-maker suddenly leaves the party or makes an unpopular suggestion, the algorithm quickly appoints another friend to take over. This way, the decision-making process continues smoothly, maintaining the network's stability and security even in the face of unexpected challenges.
Why do we need DVT? What are the benefits?
Decentralization is fundamental to blockchain technology, and DVT plays a pivotal role in bolstering network resilience. Key advantages of DVT include:
Preventing single-validator failures: By distributing the validator responsibilities, DVT side steps stability issues and missed rewards that occur when individual validators go offline.
Reducing slashing risks: Slashing events in active-passive setups can pose significant concerns. DVT lowers the probability of simultaneous node attestations due to errors.
Securing validator keys: DVT decreases the likelihood of hackers stealing keys and causing slashing by minimizing the need for internet-connected validator nodes, enhancing overall network security.
Lowering barriers to entry: The 32 ETH requirement can deter individual validators. DVT promotes participation by removing technical and financial obstacles, enabling more users to contribute to the network.
Mitigating centralization risks: By addressing factors contributing to centralization, DVT reduces stake and client centralization risks.
One advantage worth singling out is that DVT allows for active-active setups that reduces slashing risk. Normally, Ethereum validators have active-passive setups. This means backup nodes stay offline while the active node is online.
With a distributed validator setup, in-house validators can distribute their signing power across multiple nodes in an Active-Active cluster redundancy arrangement, minimizing the risk of failure and penalties due to downtime or double-signing.
Going back to our pizza party analogy, consider a group of friends who are in charge of the music and audio systems. In an active-passive setup, one person plays music, while another takes over if needed, causing a brief silence. Though insignificant at a party, in validator terms, this could lead to missed rewards or penalties. If both friends played music simultaneously, it would create an unpleasant experience, akin to a "slashable" offense in Ethereum.
DVT allows for active-active redundancy. In the case of the party, multiple speaker systems would play music simultaneously and harmoniously, ensuring uninterrupted music if one fails. In the context of validators, running multiple machines in an active-active setup ensures that even if some nodes fail, the group can still carry out its validation duties without risk of being penalized.

Who are the main players?
1. SSV Network
SSV began as a joint research project with the Ethereum Foundation in 2019. On March 30, 2023, SSV Network introduced Jato, the latest iteration of public testnet.
The SSV network creates multiple KeyShares for a validator key that runs across independent nodes. SSV acts as an intermediary between a Beacon Chain node and a validator client. It handles the splitting and distribution of a validator key and utilizes KeyShares on multiple nodes to reconstruct a data signature. To ensure security and fault tolerance, a majority of nodes are required to recreate the key for signing. For instance, in an SSV setup with four nodes, three of them are needed to recreate a validator key signature.
SSV has two distinct layers:
SSV Peer to Peer (P2P) network layer: This is the execution layer. It reads the current operator list and validator KeyShare assignments from the Ethereum smart contracts and operates the validators on the network.
Ethereum contract layer (for network governance): SSV operators will be assessed and ranked, resulting in a decentralized and transparent network score of their quality, experience, and service. Actions like adding an operator, creating a validator, and distributing fees occur on the contract layer.
More interestingly, SSV Network also has its live token $SSV. It has a total supply of 10 million and is trading at $36.5 at time of writing. The primary use cases of $SSV are for payments and governance within the network:
Payments: Stakers can use $SSV to compensate operators for managing their validators.
Governance: $SSV allows for participation in decision-making and treasury allocation within the network. $SSV plays a crucial role in motivating and engaging the community to contribute to the network’s growth.
Operators here refer to the users that maintain SSV nodes running validators on behalf of stakers to generate ETH rewards for them. In return for their services, operators receive SSV tokens from stakers. Stakers on the other hand, put 32 ETH at stake on the Beacon Chain and own a validator. Stakers pay fees to operators in SSV tokens. The economic model here is similar to networks like The Graph and Chainlink.
2. Obol Network
Obol Network is a multi-operator validator network that aims to decentralize Ethereum staking. Obol is right now in the Bia public testnet phase, followed by the mainnet launch. In terms of progress, Obol is slightly behind SSV.
The Obol Network consists of four core components:
DV Launchpad: Command Line Interface (CLI) tool and User Interface that streamlines the process of setting up Distributed Validators.
Charon: Middleware client allows validators to operate in a fault-tolerant, distributed manner, enhancing the overall stability and resilience of the network.
Obol Managers: Solidity contracts that enable the formation of Distributed Validators
Obol Testnets: A series of ongoing public incentivized testnets provide operators the opportunity to test their deployments before committing to the mainnet Obol Network
Obol can be considered as an additional layer in the standard Ethereum validator client stack, which replaces a single entity with a collective. Below is an example of the stack of a distributed validator node.
These nodes then form a distributed validator cluster, which is a collection of distributed validator nodes connected together to service a set of validators generated during a distributed validator key (DVK) ceremony.
Obol does not have a token and they have indicated that their business model will rely on taking a percentage cut from the yield the validators are receiving from staking.
While SSV Network and Obol are the frontrunners in the DVT landscape, there are a few newer smaller projects that are worth mentioning.
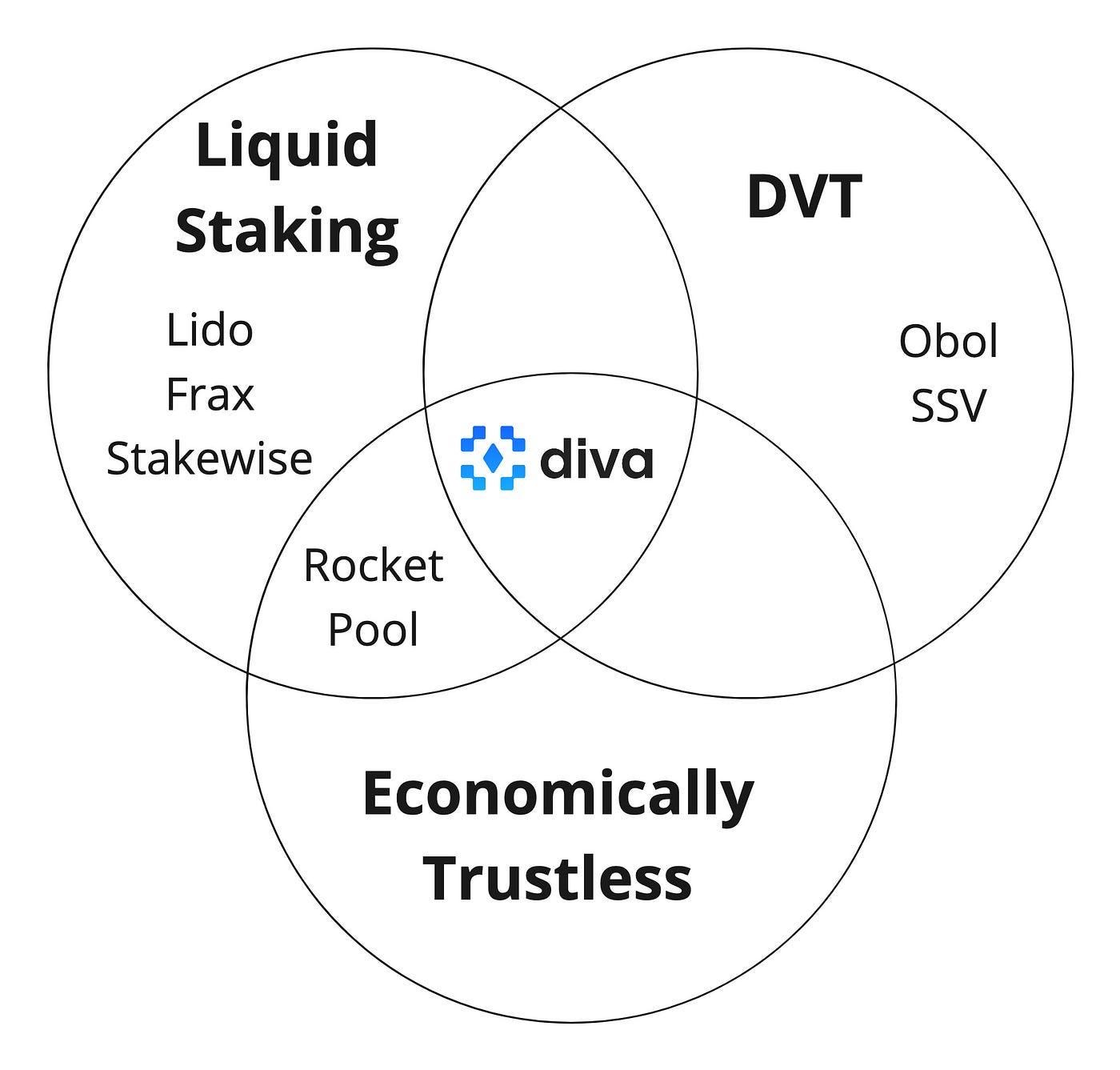
3. DIVA Labs
Diva aims to merge LSD and DVT models to develop a comprehensive solution for liquidity staking and distributed validation.
When ETH is deposited into Diva it is combined with other deposits to satisfy the Ethereum Validators 32 ETH requirement. These validators are managed by the Node Operators, using Diva’s P2P consensus layer. DVT solutions are designed as middleware for existing staking setups, with no economic mechanisms linking stakers and DVT operators to each other’s success in a trustless and permissionless manner. Diva seeks to build a vertically integrated product that is simple and easy to use.
4. Stader Labs
Stader Labs is a non-custodial smart contract-based staking platform that is building staking middleware infrastructure for multiple PoS networks. They have recently announced their plans to be early adopters of Distributed Validator Technology. Stader Ethereum has also mentioned that their ETHx design has a multi-pool architecture for three different node operator models, including DVT stake pool. They are already in testnet with SSV Network.
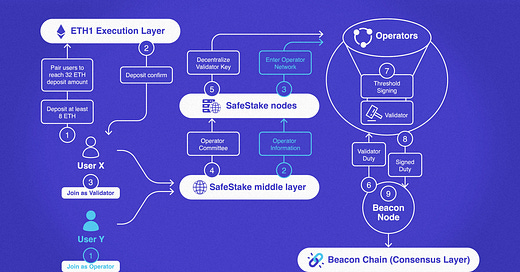
5. Safestake
SafeStake is a decentralized staking infrastructure and protocol designed to maximize staker rewards by ensuring validators remain secure and online for Ethereum staking duties. As a turnkey DVT solution, it splits validator keys into shares and distributes them across multiple nodes, achieving high levels of security and fault tolerance.
What are the trade-offs with DVT?
While DVT offers numerous benefits, it also comes with certain trade-offs that must be considered.
First, the increased complexity of a multi-node deployment means there are more moving parts in running a validator as a whole. Another trade-off is increased latency, as DVT introduces additional network hops due to the consensus mechanism and message sharing across nodes in a cluster. However, this is mitigated by designing DVT to use direct P2P connections across nodes in a cluster (rather than a singular gossip network).
There are operational costs to consider, as multiple nodes are required to participate instead of just a single node. On the other hand, this can be offset by the ability to run more validators on the same set of machines due to the improved resiliency of validators running DVT.
Can DVT be the next big narrative for Ethereum?
Major liquid staking protocols are already recognizing the potential advantages of DVT and have initiated pilot tests on their networks. This exploration is critical in demonstrating the effectiveness and potential benefits of DVT to the wider community. DVT could enhance efficiency and reduce risk for liquid staking protocols while boosting operator participation. By offering network redundancy, it eliminates reliance on a single operator, preventing downtime. Operators, organized into clusters, ensure that if one fails, others maintain attestation thresholds, keeping validator nodes unaffected.
As liquid staking protocols shift towards greater decentralization, Rocket Pool, Stakewise V3, and Lido V2 are beginning to adopt a modular approach that grants users more control over validator node configurations. This transition could be further augmented by DVT, which plays a central role in the design of increasingly decentralized specifications.
However, it is important to note that the business and token models for DVT are still being refined. For example, the SSV Network utilizes its native token for payments, while Obol Network is considering taking a percentage of staking rewards as part of its revenue model. The evolution and iteration of these models will play a significant role in the widespread adoption of DVT.
What is clear is that DVT directly addresses the challenges associated with ETH staking and promotes true decentralization on the Ethereum platform. With DVT, validators are better equipped to meet the safety and liveness requirements necessary for a secure and efficient network. As we look to the future, it is reasonable to envision a scenario in which many of the leading liquid staking providers adopt DVT for a substantial portion of their validators within the Ethereum network.
The Shanghai/Capella upgrade represents a major milestone for Ethereum. With withdrawals enabled, market participants can effortlessly switch between staking products, reducing friction. This lower risk profile may entice more stakers to join the ecosystem, resulting in a higher staking ratio for Ethereum. DVT serves as a critical infrastructure component that stands to gain from the upgrade and has the potential to drive the next wave of innovation and growth in the staking landscape.
References
Ethereum Staking
Staking statistics
Distributed Validator Technology
What is DVT and why is it important for Ethereum’s decentralization?
Distributed Validator Technology — The Next Ethereum Roadmap Narrative? | by Moonrock Capital
LSD and DVT: Pioneering Technologies Changing the Future of Cryp… — veDAO
Easy and secure staking with Distributed Validator Technology | ethos.dev
Distributed Validator Technology on Eth2 | by Mara Schmiedt | Coinmonks
Sorting out Distributed Validator Technology - Nethermind.eth - Medium
Distributed Validators: Improving Staking No Matter Your ETH Balance
Obol Network
SSV Network
The Secrets behind Secret Shared Validator (SSV) Technology | ssv.network
SSV Network (SSV): Transforming ETH Staking | Bybit Learnssv.network Price Prediction | Is ssv.network a Good Investment?
The Secrets behind Secret Shared Validator (SSV) Technology | ssv.network
Disclaimer
The Blockcrunch Podcast (“Blockcrunch”) is an educational resource intended for informational purposes only. Blockcrunch produces a weekly podcast and newsletter that routinely covers projects in Web 3 and may discuss assets that the host or its guests have financial exposure to.
Some Blockcrunch VIP posts are written by contractors to Blockcrunch and posts reflect the contractors’ independent views, not Blockcrunch’s official stance. Blockcrunch requires contractors to disclose their financial exposure to projects they write about but is not able to fully guarantee no such conflicts of interest exist. Blockcrunch itself will not buy or sell assets it covers 72 hours prior to and subsequent to the publication of a piece; however, its directors, employees, contractors and affiliates may buy or sell assets prior to or subsequent to publication of any content and will make disclosures on a best effort basis.
Views held by Blockcrunch’s guests are their own. None of Blockcrunch, its registered entity or any of its affiliated personnel are licensed to provide any type of financial advice, and nothing on Blockcrunch’s podcast, newsletter, website and social media should be construed as financial advice. Blockcrunch also receives compensation from its sponsor; sponsorship messages do not constitute financial advice or endorsement.
For more detailed disclaimers, visit https://blockcrunch.substack.com/about